Until now, our network security has been very static. We created security policies based on source IP addresses, destination IP addresses, and ports.
Continue reading
The story of Rubaruba's network at the edge
The EASY EDGE story

Until now, our network security has been very static. We created security policies based on source IP addresses, destination IP addresses, and ports.
Continue reading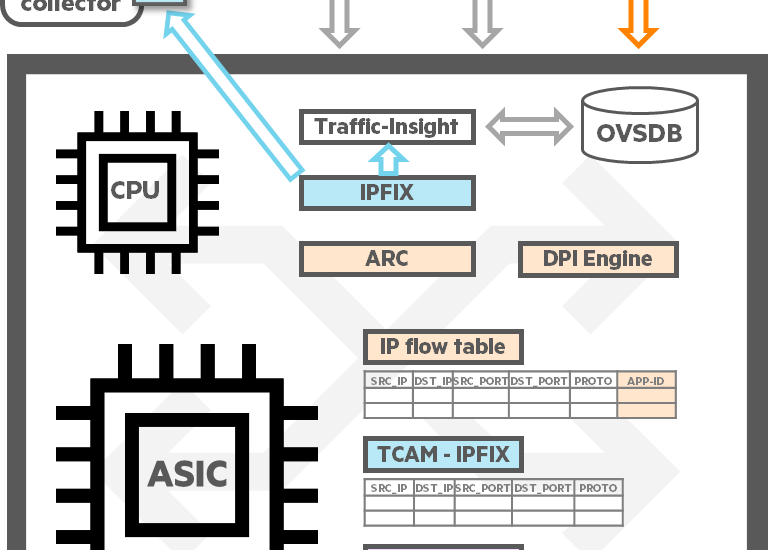
As the complexity of IT infrastructure increases, more and more devices are connected to the network. Network operators are concerned about which devices are connected.
Continue reading