Network traffic patterns within data centers are changing recently.
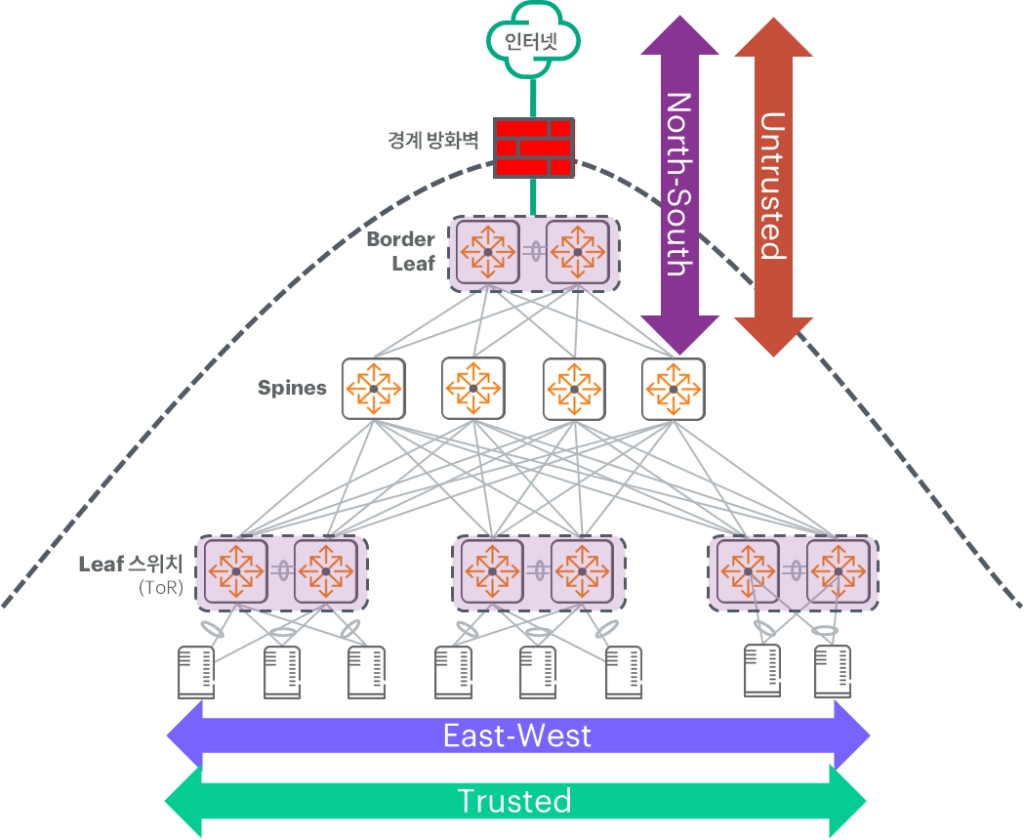
Traffic originating within the data center (East-West) is becoming far more important than traffic between the data center and the outside world (North-South).
This shift is being accelerated by the proliferation of technologies that rely heavily on communication between servers and resources within data centers, such as virtualization, cloud computing, and microservices.
Data Center Network Modernization: A Business Imperative for Secure, Flexible Operations
In today's digital economy, data centers are more than just IT infrastructure; they are strategic assets that drive innovation and competitive advantage.
However, with the rapid increase in intra-data center traffic (east-west traffic) due to virtualization, cloud adoption, and containerization, serious security vulnerabilities and operational inefficiencies are being exposed.
Focused on internal and external traffic Traditional perimeter-based security models are ill-equipped to handle the dynamic and interconnected nature of modern data centers.These gaps pose significant risks to business continuity, data integrity, and regulatory compliance.
The East-West Traffic Surge: Invisible Network Conversations
Imagine your data center as a bustling city.
Traditional security focused on the city's perimeter, keeping outsiders out. This is North-South trafficno see.
But inside the city, there is a much more complex and massive traffic, and this is East-West trafficno see.
This 'East-West traffic' refers to communication between servers, applications, and microservices within a data center.
In today's interconnected world, applications are no longer monolithic.
Countless small components work together, constantly exchanging data.
Let's take online ordering as an example.
The website communicates with the inventory database, which in turn communicates with the payment processing system.
All of these conversations take place inside the data center, and East-West TrafficIt is called.
The following factors are behind this explosive increase in internal communications:.
- Virtualization: Unlike the past when we used one server per application, now we have many virtual servers that need to communicate with each other.
- Cloud computing: Cloud environments require internal communication, as applications and data are distributed across multiple servers.
- container: Technologies like Docker and Kubernetes divide applications into independent containers, each of which communicates with the others.
- Microservices: Modern applications are made up of microservices that communicate with each other to perform tasks.
The surge in east-west traffic creates a much wider attack surface.
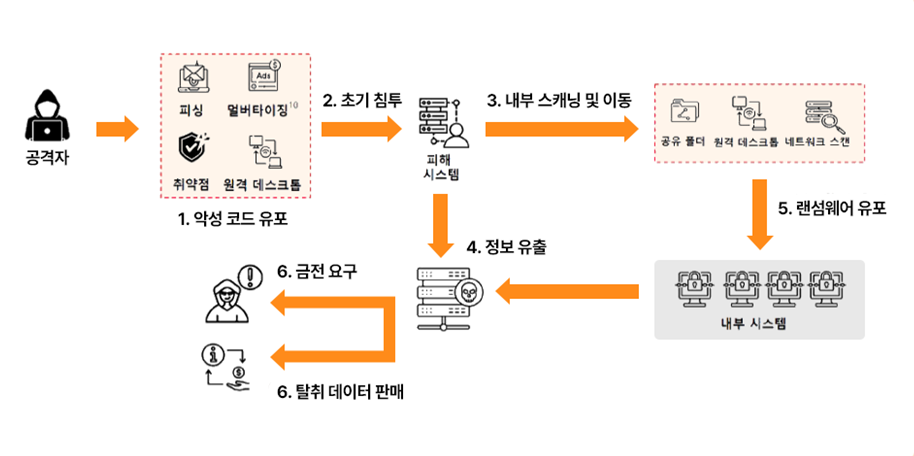
If an attacker breaches one server, they can easily access sensitive data on other servers by exploiting the interconnectivity of the network. lateral movementIt's like an intruder entering a building and then being able to freely come and go from any room.
The Impact of Unsecure East-West Traffic on Your Business
Even for business leaders who aren't security experts, unsecured east-west traffic poses a serious problem.
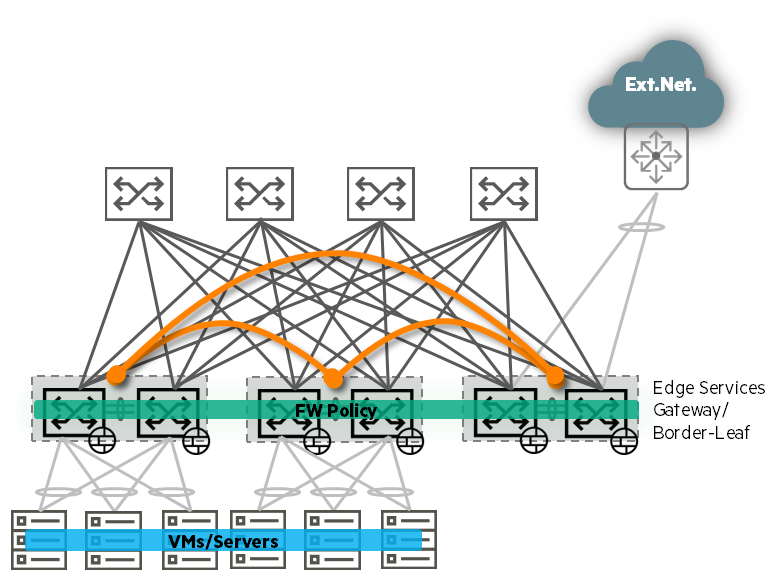
- Increased likelihood of breach: Lateral movement of threats within a data center can result in catastrophic data breaches that lead to significant financial losses, reputational damage, and regulatory violations.
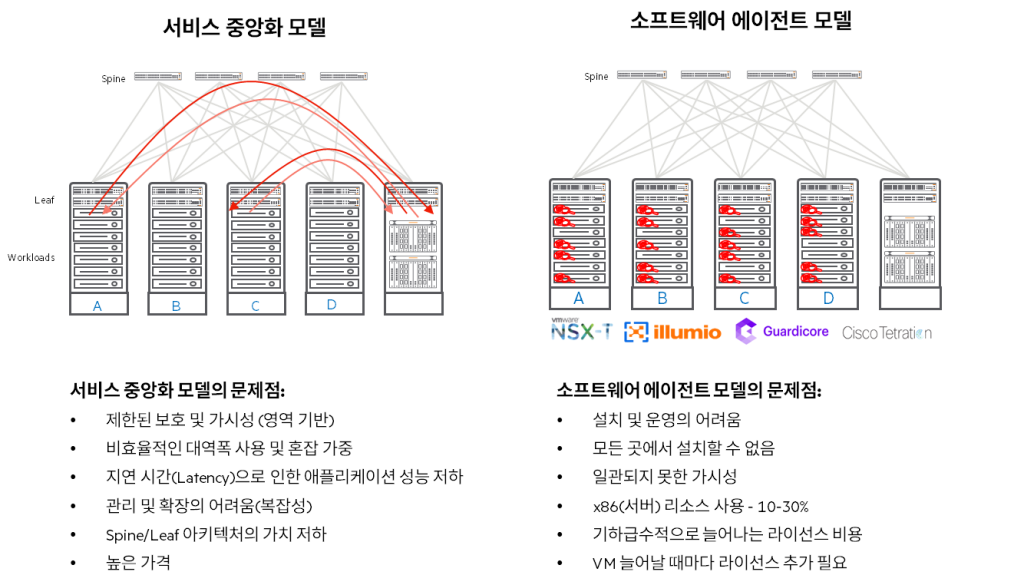
- Operational Bottlenecks: Traditional security architectures cause performance degradation, degrading application performance and slowing down business processes. Imagine filtering all internal conversations through a single, centralized point. This would inevitably result in delays and inconvenience.
- Compliance issues: Failure to implement granular security controls can lead to noncompliance with industry regulations, resulting in significant fines and legal penalties. Regulators are increasingly paying attention to how companies protect data on their internal networks.
- Decreased agility and innovation: Ineffective security architecture hinders the rapid deployment of new applications and services, hindering business agility and innovation. Internal networks that create security and performance bottlenecks make it difficult to quickly respond to market changes.
Microsegmentationand East-West Traffic Control: Strategic Investments for Business Resilience
To mitigate these risks and ensure business resilience, you must adopt a modern, software-defined data center security approach.
Microsegmentation and East-West traffic control are not simply technology solutions; they are strategic investments that deliver significant business benefits.
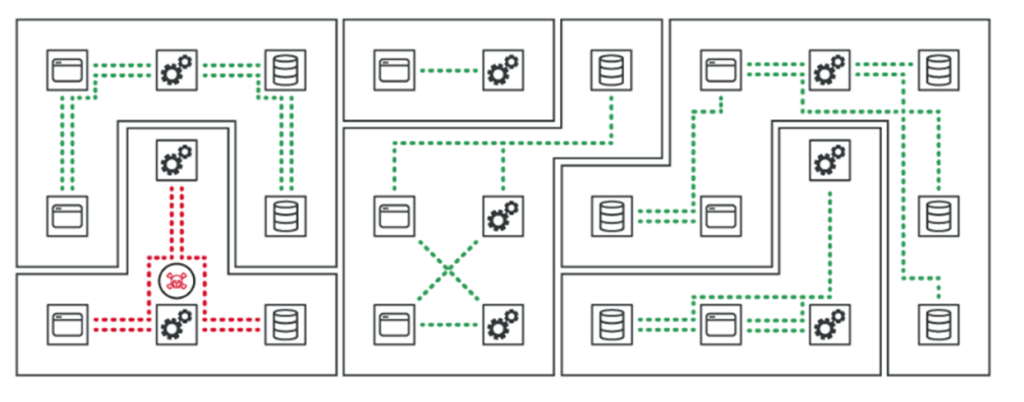
“Strong perimeter security is not enough. Modern systems can span more than one DC/cloud.
As the attack surface expands and the potential for breaches increases, prevention becomes increasingly difficult, if not impossible.”
- Enhanced security: By limiting lateral movement and enforcing granular security policies, we minimize the impact of a breach and protect critical business data and applications. It's like creating a firewall for each individual "room" within a data center, preventing intruders from moving freely.
- Improve operational efficiency: Distributing security functions to the network edge and reducing reliance on centralized firewalls eliminates bottlenecks and improves application performance.
- Simplify compliance: Granular controls enable you to meet stringent regulatory requirements and reduce compliance risks and costs. Precise controls demonstrate to regulators that you strictly manage internal data flows.
- Improve business agility: A flexible and scalable security architecture facilitates innovation and competitive advantage by enabling the rapid deployment of new applications and services. It makes it much easier to adapt to new business needs.
Data Center Networking Innovation: A Business-Driven Approach
Implementing these technologies requires a strategic and business-focused approach.
- Business Risk Assessment: Identify your core business assets and assess the potential impact of security breaches and operational disruptions.
- Develop a strategic plan: Align security initiatives with business objectives and prioritize those that deliver the greatest return on investment.
- Step-by-step execution: We are gradually introducing microsegmentation and east-west traffic control to minimize the impact on business operations.
- Continuous monitoring and optimization: Leverage real-time measurement data to continuously monitor network performance and security status, and continuously optimize security policies to meet changing business needs.
- Secure executive sponsorship: Drive cultural change across the organization with executive sponsorship and ensure alignment between IT and business.
conclusion
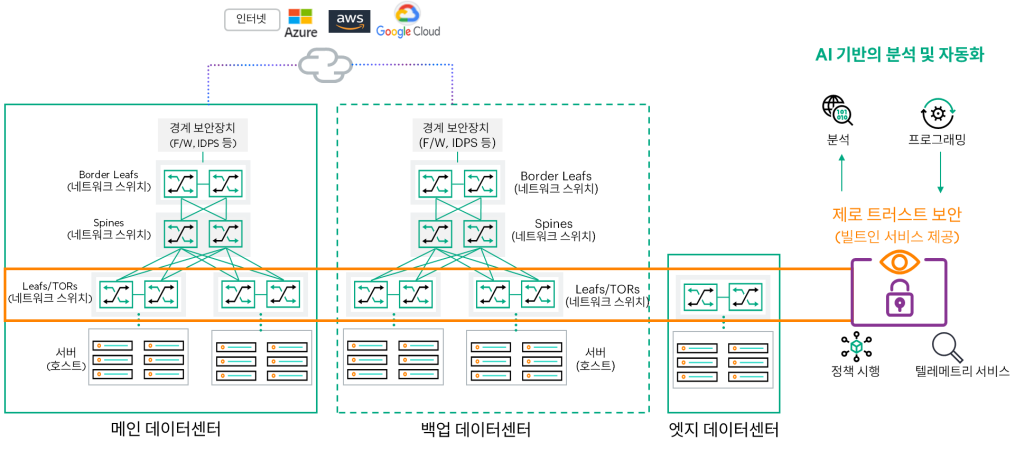
Modernizing Data Center Networks with Microsegmentation and East-West Traffic Controlis not simply a technology upgrade; it's a business imperative. By prioritizing security and agility, companies can protect core assets, improve operational efficiency, and drive sustainable growth in the digital age.
These changes require a business-centric, strategic approach to ensure IT investments align with overall business objectives and deliver tangible results.


