Two months have already passed in 2025 and March has begun.
Looking back on last year, it's undeniable that it will be remembered as a year in which AI rose to prominence.
Many companies are accelerating the adoption of AI-based solutions to increase efficiency, streamline operations, and enhance user experiences.
The rise of AI, changing market conditions, intense competitive pressures, and ever-increasing cyber threats are all top considerations for companies when planning their technology investments.
Building on this growth and anticipation, we explore five trends expected to have the greatest impact on networking and security in 2025.
Prediction 1: Data will be recognized as a key asset for AI, rather than GPUs.
When people think of AI, GPUs, which are often used to train large-scale language models, often come to mind first.
And when you think of networking for AI, you think of the GPU-to-GPU connections used in training systems, such as InfiniBand or 800Gbps Ethernet.

GPUs and interconnects are essential components for implementing the AI ecosystem, but the power that powers these models Quality and quantity of data Equally important, the extensive network outside the data center plays a key role in collecting and aggregating telemetry and other data necessary for AI analysis and decision-making.
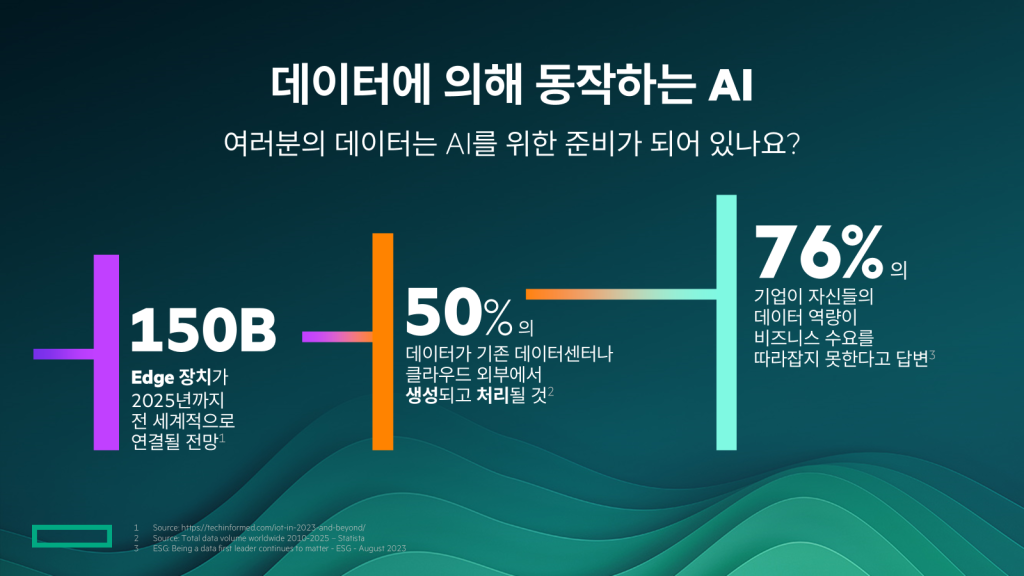
Because the variety and quantity of data influences outcomes, companies will tend to collect more data.
As a result, organizations will increasingly focus on ensuring their networks are powerful enough to handle the data required for AI models.
Prediction 2: Networks will become the security solution.
When the Internet first began, the role of the network was to connect every endpoint to every other endpoint.
At that time, a university professor could access an Internet server from anywhere in the world.
But as connectivity spread into the workplace, companies recognized that security was essential to keep out intruders, and the firewall was born.
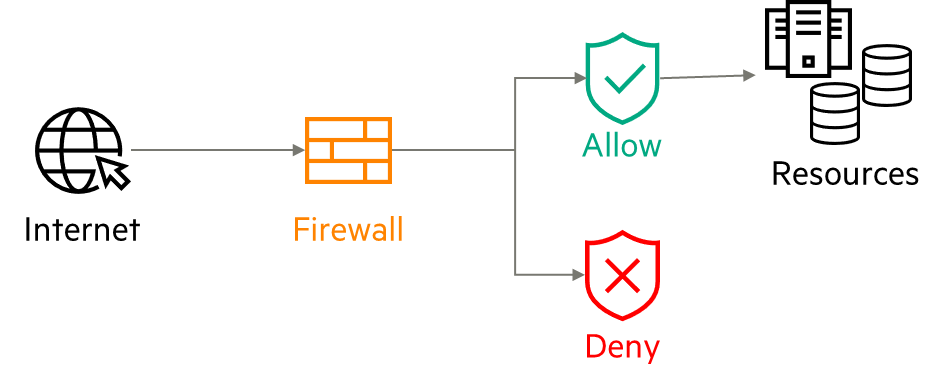
Firewalls were initially designed to protect network resources by controlling inbound and outbound traffic, and later to segment internal networks to protect some resources, preventing malicious actors from moving laterally within an organization.
Firewalls have proliferated over the past few years as networks have become more segmented to address increasing security threats, and now enterprises are looking for ways to streamline security implementation. The good news is that simplification is possible as firewalls and network segmentation are embedded in access points, switches, and gateways, and these devices are controlled by a unified corporate policy.
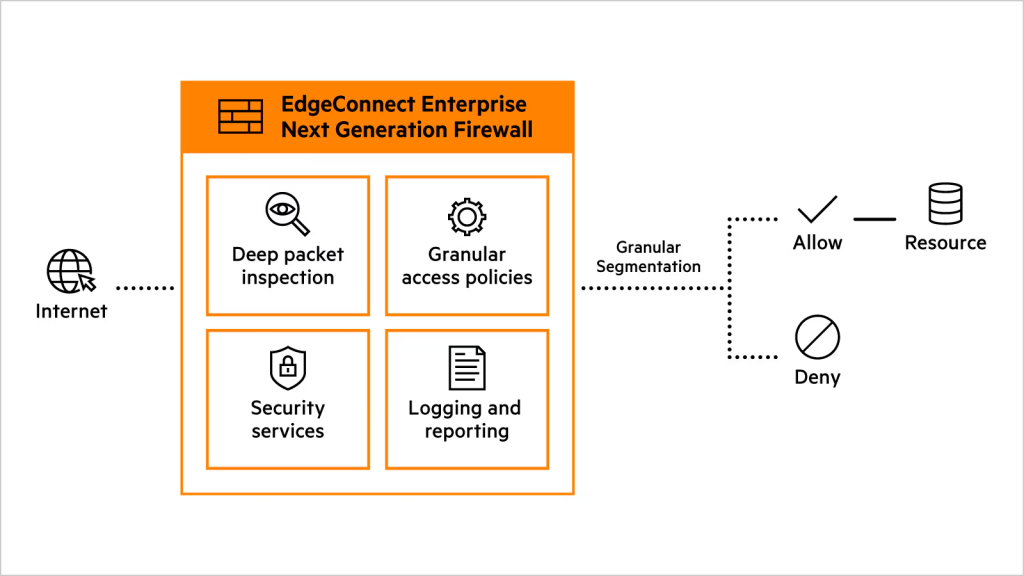
The real catalyst here is the adoption of zero trust networking. Zero trust networking is more than just a buzzword.
Zero Trust Networking provides a path to more clearly separate the definition of security policy from its enforcement.
Security policy remains the responsibility of the CISO and the security organization.
But instead of applying thousands of ACLs to each of your numerous firewall devices, you can now implement policies on the network itself.
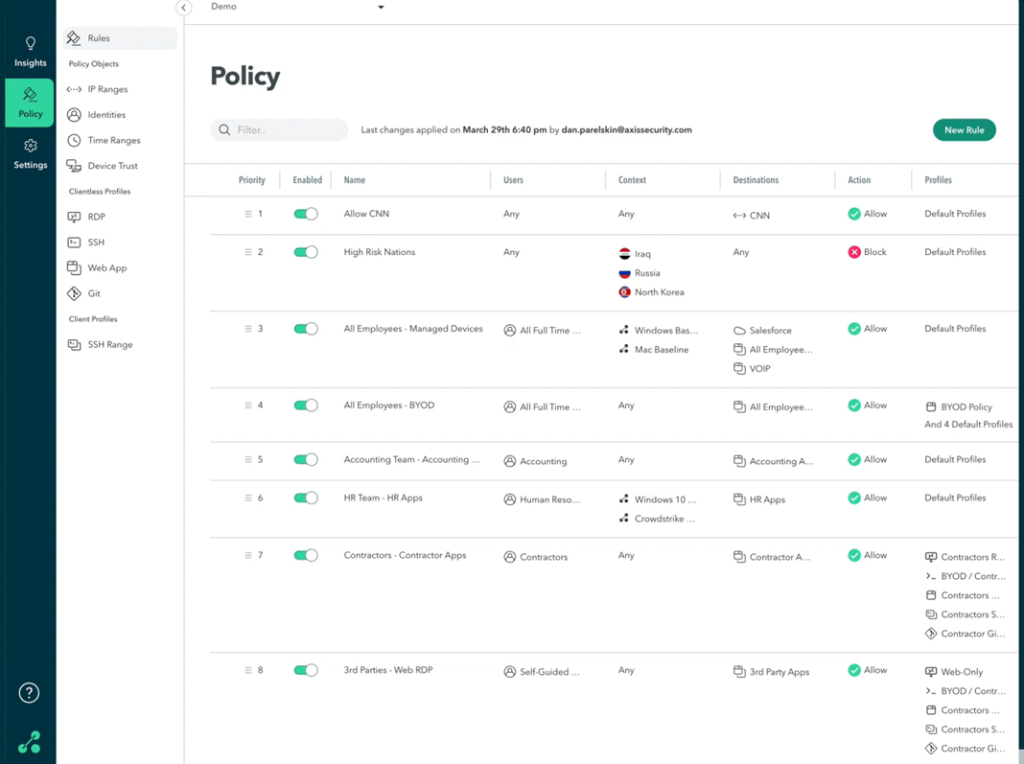
In other words, the role of the network is to fundamentally not connect anything and only allow connections that match its security policy.
Compared to a firewall-based approach, this "network as a security solution" approach can streamline operations for both IT and security teams.
Prediction 3: Integrated security controls across on-premises and off-premises.
Hybrid work environments with users accessing the network from multiple locations are a reality for most businesses.

Traditionally, IT teams have treated remote users as a special case, distinct from on-premise users. Differing policies have led to differing experiences and complexities for users, especially the vast majority of hybrid users who work remotely while also commuting to the office.
Universal Zero Trust Network Access (U-ZTNA) solutions provide a path to unified experiences. By universally applying the same identity-based rules regardless of location, you can improve security posture and user experience consistency.
Today, ZTNA solutions are primarily deployed to secure remote users, and policies are typically enforced at a cloud PoP (Point of Presence). Applying these solutions to on-premises users requires redirecting all traffic to the cloud PoP.
If your target application is hosted in the cloud, it makes sense to use the cloud PoP as a transit point for policy enforcement.
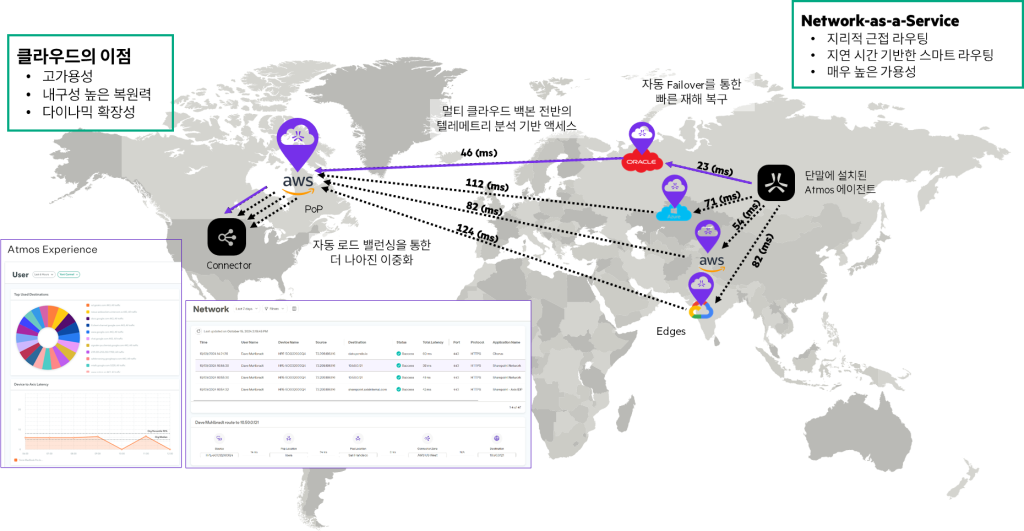
However, if the applications or resources being accessed are on-premises, 'trombone routing' through PoPs can be inefficient.
This is also unnecessary, as general-purpose ZTNA solutions are evolving to enable the same policies to be applied on-premises, relying on the security built into the network described above.
Finally, a complete, universal ZTNA solution can enforce policies not only on individuals accessing applications, but also on IoT devices. Traditional ZTNA solutions typically use client agents or browsers to intercept session establishment, redirect traffic to a cloud POP, and enforce identity-based policies.
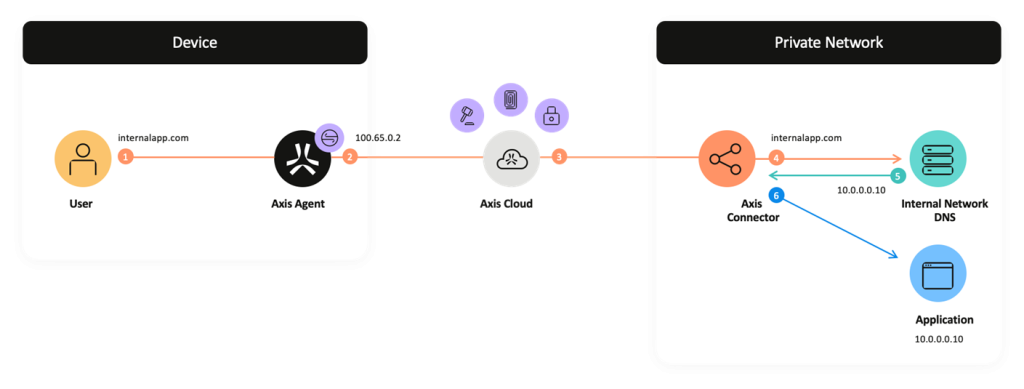
It would be ideal if we could do this on IoT devices as well, but most IoT devices are closed and cannot install agents.
In other words, a different approach is needed.
A general-purpose ZTNA for IoT requires on-premises terminal authentication and continuous monitoring.
Ideally, on-premises implementations are also required, reinforcing the trend of building security into the network.
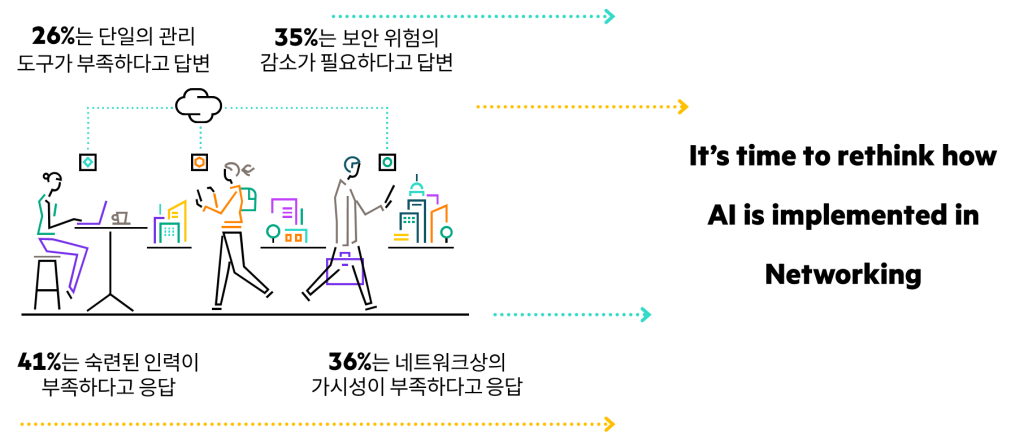
Prediction 4: AI Enables Faster Network Technology Adoption
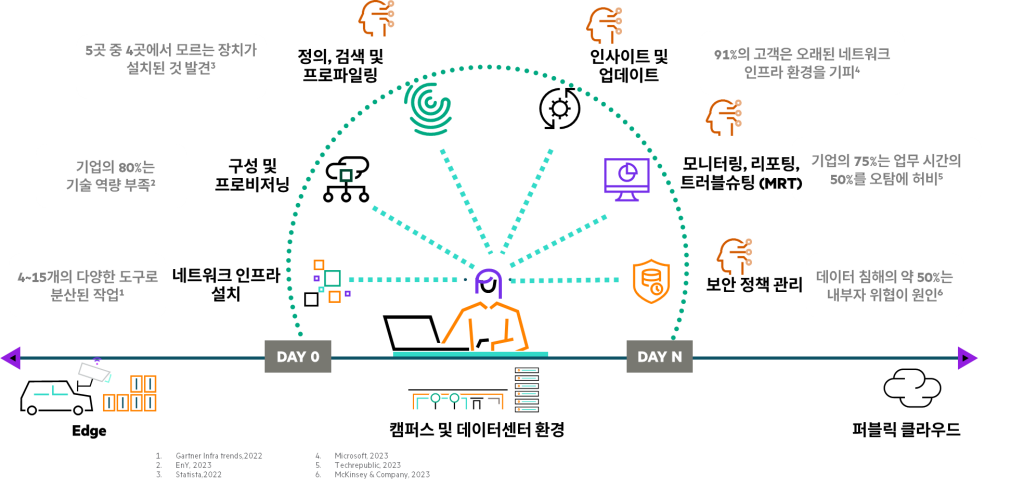
For decades, becoming a network administrator required memorizing complex CLI commands, obtaining professional certifications, and dedicating significant time to keeping your knowledge base up to date. The more time you spent maintaining your skills, the less time you had to focus on the problems your business was trying to solve or the experiences your users wanted.
AI is what can solve these problems.
Using AI, managers can define goals they want their AI assistants to achieve, and the assistant can provide immediate help and even suggest solutions to problems.
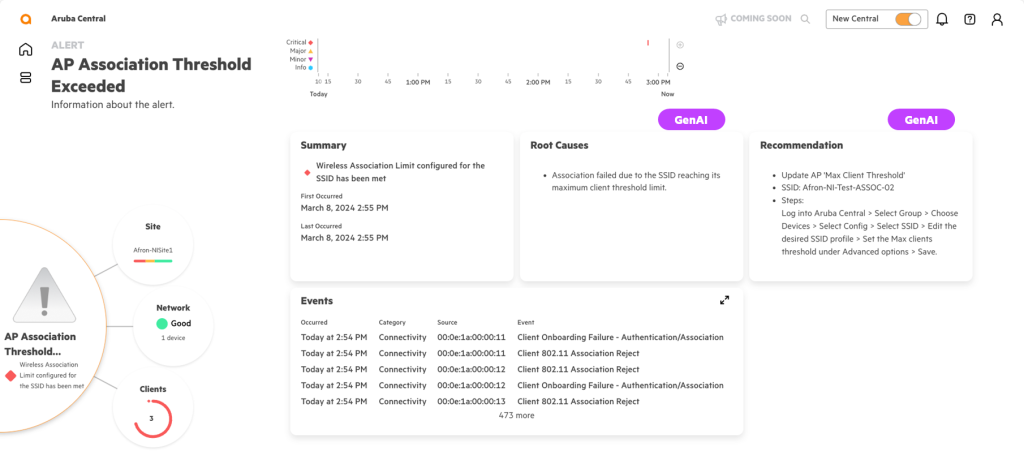
Additionally, administrators don't need to memorize complex CLI commands, and solutions can be applied across specific networks or groups of devices without having to customize the CLI for each device. Furthermore, parameters can be automatically adjusted based on learnings generated from data collected from millions of devices to maximize network performance.
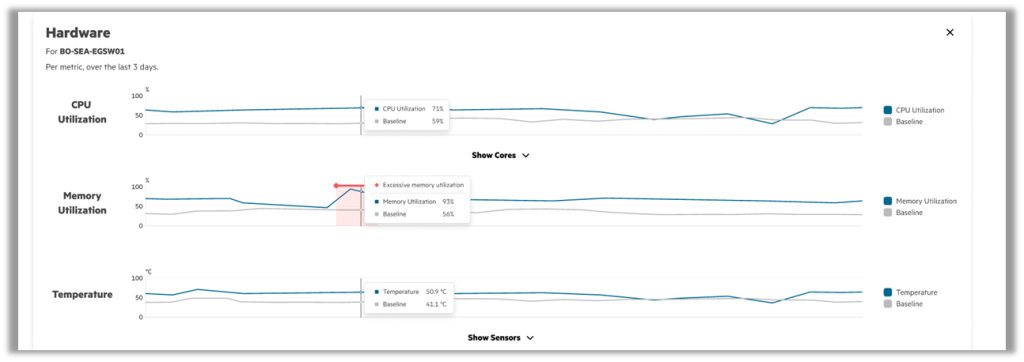
All of this frees IT managers from the shackles of legacy infrastructure by accelerating the adoption and optimization of new technologies.
Prediction 5: AI-Ops Expands to Support Multivendor and Multidomain IT
Almost every network vendor is talking about how they're using AI in their management platforms.
While each vendor claims similar features and benefits, these platforms currently offer benefits only for basic networking functions.
Therefore, the scope of AI's influence is limited because it cannot see the 'invisible' third-party infrastructure.
Many customers are looking for a single AI-powered platform that can provide visibility and insights into equipment from multiple manufacturers.
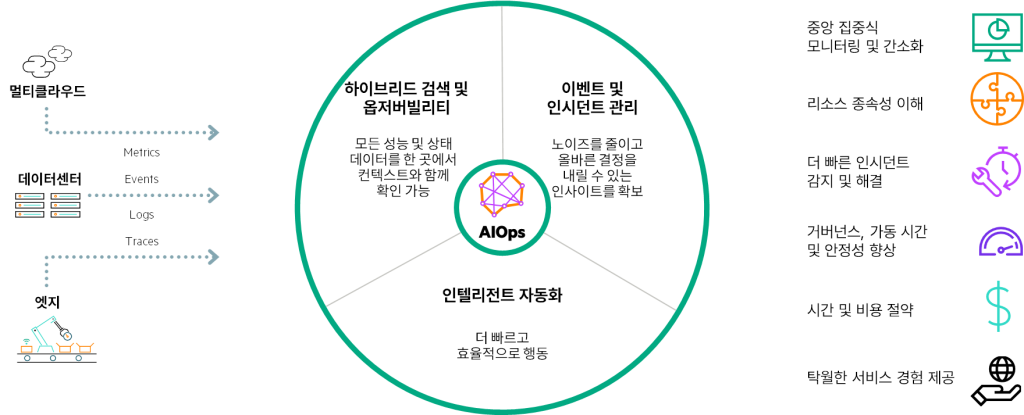
This trend extends to the network realm.
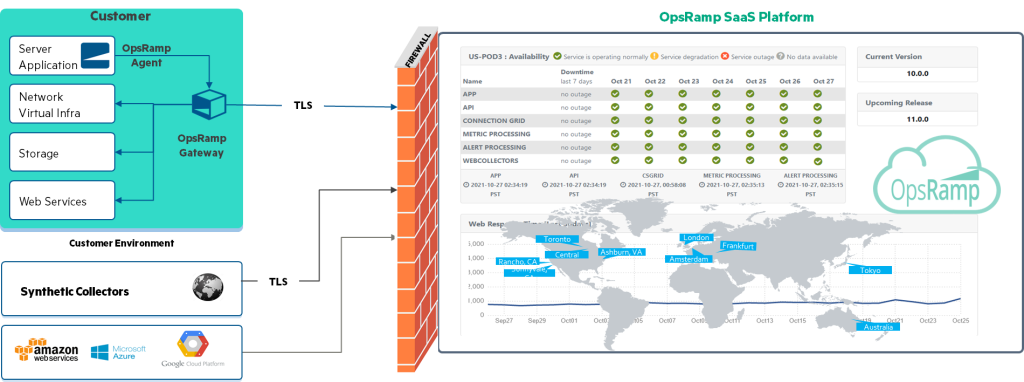
Enterprises want to correlate and identify cross-domain issues across compute, storage, and networking, leveraging telemetry data from all these sources to deliver better outcomes.
The power of AI in this field has yet to be fully realized, and it's exciting to see the momentum building this year.
Since COVID-19, IT infrastructure has become increasingly busy and chaotic, driven by the changing environment.
This year, expect continued innovation and change to help your business grow and thrive, and be brave enough to embrace new solutions.