Research shows that 66% organizations were impacted by ransomware last year.1
So, can you spot the signs of a ransomware attack in advance?
Discovering data encryption and demanding a ransom may be the most visible signs of a ransomware attack, but they actually occur at the end of the attack.
To protect against ransomware, you need to build layers of defense to detect attacks early and accelerate ransomware recovery.
The first step to building an effective defense is understanding how ransomware attacks work.
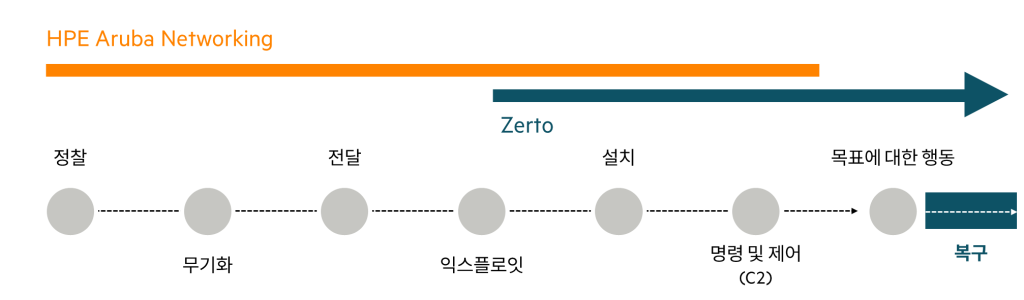
Hacking Life Cycle
Ransomware attacks follow a common pattern, called the kill chain or hacking lifecycle.
The hacking lifecycle consists of seven stages of malicious activity.
Each step helps hackers systematically explore and exploit vulnerabilities in the target system without being detected.
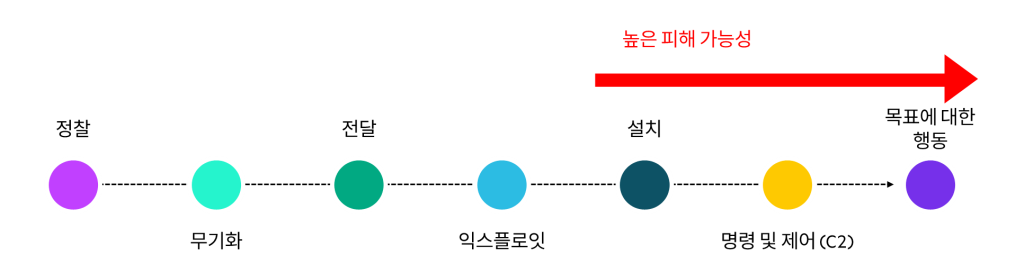
Stage 1 reconnaissance
Hackers collect data about their targets and vulnerabilities they can exploit.
Tactics include finding systems with unpatched vulnerabilities, performing social engineering to learn about users and internal processes, and scanning networks to find exposed systems.
Step 2: Weaponization
Hackers use the information gathered through reconnaissance to create or repurpose malware to exploit discovered vulnerabilities.
Potential tools for weaponization could include viruses, worms, exploit kits, and similar malware.
Step 3: Delivery
Attackers can use tactics like "drive-by downloads," installing infected software, and phishing to trick users into unknowingly introducing malware into their systems. For example, if an employee receives an email containing malware hidden behind a seemingly legitimate attachment, clicking the attachment will execute the malware and compromise the system.
Step 4: Exploit
Once the malware payload is delivered, the attacker attempts to gain a foothold within the victim's network.
This stage of the attack can continuously expand the attack surface by disabling security systems that monitor for security threats and unauthorized access.
Step 5: Installation
Once a 'base' is established, the potential for damage increases significantly.
The attack could propagate, resulting in persistent unauthorized access to additional systems.
Attackers can escalate privileges to penetrate deeper, disable firewalls, and install additional malware.
Step 6: Command and Control
Now, the attacker has penetrated the victim's internal network and established a communication link between the compromised systems and the attacker's central infrastructure, allowing them to remotely manage systems, issue commands, exfiltrate data, and move laterally throughout the victim's infrastructure.
Step 7: Take Action on Your Goals
At this stage of the hacking lifecycle, the attacker has successfully breached the target and can now achieve their attack objectives.
Attackers' goals can vary, but can include data theft, system compromise, operational disruption, and even extending the attack scope to connected third-party systems, as in the case of supply chain attacks.
Attackers can contact victims and force them to pay a ransom.
Ransom demands can be accompanied by threats of data breaches, reputational damage, additional attacks (e.g., DDoS attacks), and more recently, extortion and harassment of the victim's employees, customers, patients, or students (double and triple extortion attacks) to pressure the victim into paying the ransom.
In 2023, organizations paid a record high of over $1 billion in ransoms.2
The Role of IDS/IPS in Preventing Ransomware Attacks
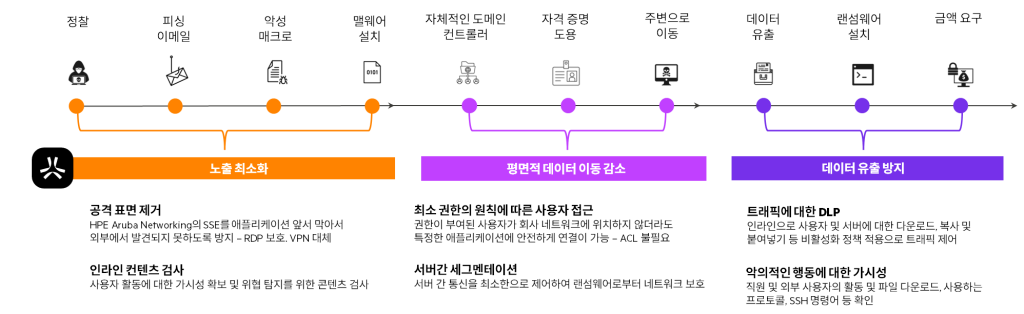
As the hacking lifecycle demonstrates, ransomware attacks begin long before a ransom is demanded.
If organizations can detect the signs of a ransomware attack early in the hacking lifecycle, they can block the attack and prevent further damage.
Intrusion Detection and Prevention Systems (IDS/IPS or IDPS, often used together) are useful tools for combating the early stages of ransomware attacks.
Monitor targeted traffic for potential threats and malicious activity.
An intrusion detection system (IDS) monitors incoming and outgoing network traffic flows for malicious and suspicious activity.
When potential threat activity is detected, the IDS can generate a threat event.
Note that IDS does not take action on identified threats.
Configuring an IDS can help you detect and capture details of detected threats.
Detect threats by analyzing traffic
Intrusion Prevention Systems (IPS) work complementarily with IDS.
IPS monitors your network for malicious activity, generates alerts, and takes action based on predefined rules.
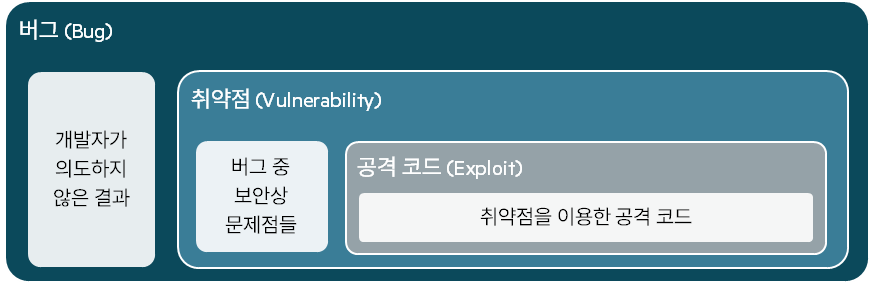
IPS can detect a wide range of threats. It can identify threats using a variety of techniques, including anomaly detection, policy-based detection, and the most common signature-based detection. Signatures are known threat patterns that can detect many ransomware-related threats, including:
- Phishing: Rules that detect credential phishing activity and successful submission of credentials to credential phishing sites.
- malware: Rules to detect software with obvious criminal intent that is in transit, active, infected, attacking, or updating.
- prejudice: Rules that identify threats from a list of known compromised hosts that are checked and updated daily.
- Exploit: Rules that detect direct exploits not covered by specific categories.
Take protective action when a threat is detected
IPS policies manage the protective actions taken when threats are detected.
Protective measures may include dropping threat packets, blocking traffic from the source of the threat, and reconfiguring firewall rules to prevent future attacks.
Generate threat events based on pre-configured rules
A threat event is any situation that could negatively impact an organization.
Organizations can configure rules within their IPS to define and categorize threat events by severity.
You can adjust the thresholds based on your organization's risk tolerance.
Distribute threat intelligence throughout the security ecosystem
Layered defense is key to defending against ransomware. Therefore, it's crucial for IDS/IPS tools to distribute high-quality threat intelligence across the entire security ecosystem.
For example, threat data recorded in HPE Aruba Networking Central can be shared with SIEM servers and other supported third-party integrations through the central alerting framework. You can also configure rules in HPE Aruba Networking Central to share information via webhooks with systems like HPE Zerto, which protects sensitive data from ransomware attacks.
To learn more about the role of IDS/IPS in ransomware, please see the links below.
- Demo: Ransomware Defense with HPE Aruba Networking Central and HPE Zerto
- Blog: Network security: First defense against ransomware
- Blog: Combatting ransomware with layered Zero Trust Security
- Learn on demand: The hacking lifecycle and protecting your data
- Global Cyber Threat Intelligence: Annual Cyberthreat Trends. Deloitte, 2024 ↩︎
- https://www.fisherphillips.com/en/news-insights/ransomware-costs-businesses-record-high-1-billion-in-2023.html ↩︎


