Rapidly evolving cyber threats continue to challenge organizations worldwide.
Legacy infrastructure, once considered robust, now struggles to withstand modern attack methods.
To address these challenges, HPE Aruba Networking offers a comprehensive suite of security solutions designed to protect users, devices, applications, data, and networks. Zero Trust Strategy Provide a portfolio.
Escalating threat environment
Cyber attackers exploit vulnerabilities in outdated network infrastructure, targeting unpatched systems and lax security policies.
A prime example is the Akira IoT ransomware attack that occurred in March 2025.
The attack exploited vulnerable IoT devices to infiltrate the organization's network.
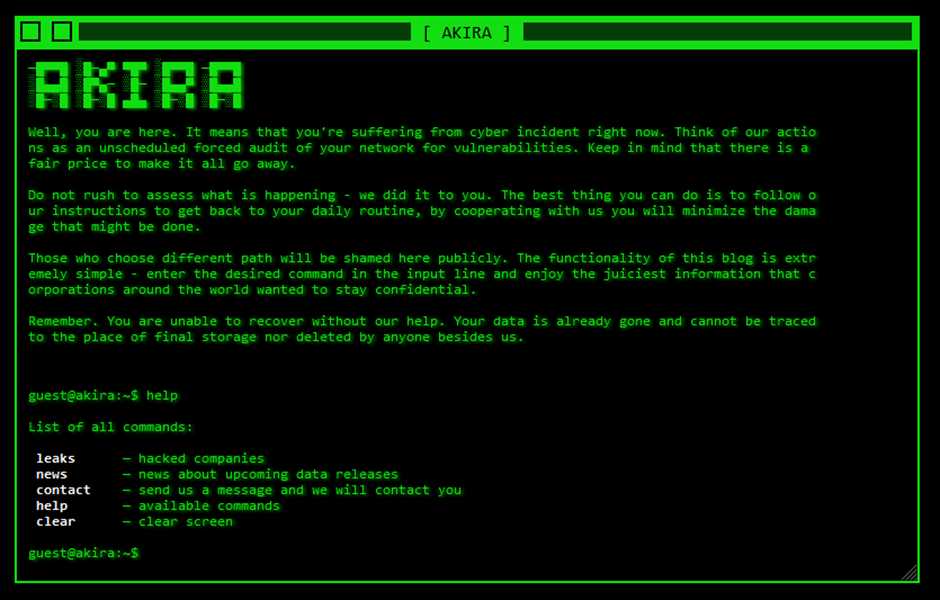
This case study demonstrates the importance of implementing modern security measures to prevent unauthorized access, detect anomalies, and block threats before they spread.
Zero Trustis a network A security model that states that no entity, internal or external, should be inherently trusted.no see.
Instead, all access requests undergo authentication, authorization, and continuous monitoring.
HPE Aruba Networking helps you apply zero trust principles across multiple layers, creating a strong defense against cyber threats.
HPE Aruba Networking's Zero Trust Approach
1. Device identification and authentication
Unmanaged or unauthorized devices are prime targets for attacks.
To prevent this, HPE Aruba Networking instantly identifies all devices and automatically blocks or quarantines any unknown or non-compliant devices.
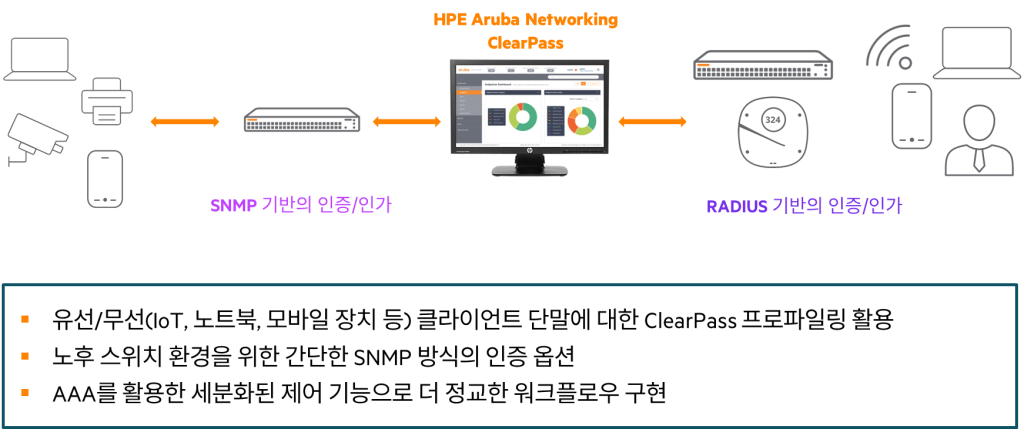
- HPE Aruba Networking ClearPass NACIt mandates authentication for devices connected to the network.
- Multifactor Authentication (MFA), Certificate-based authentication, and MAC authentication through device profilingensures that only authorized devices have access.
2. Policy-Based Access Control
Controlling the interaction of devices within a network is very important.
- Dynamic SegmentationIsolates IoT devices such as webcams from sensitive corporate systems.
- Role-Based Access Control (RBAC)blocks unauthorized communications by assigning strict policies to each device.
- Stateful firewall inspection와 HPE Aruba Networking NAEprovides continuous monitoring and policy enforcement.
3. Strengthening wireless and network security
Modernizing your network connectivity strengthens your security resilience.
- WPA3 Enterprise Securityensures strong encryption and authentication.
- Intrusion Detection/Prevention System (IDS/IPS)identifies and blocks unauthorized firmware updates.
- Wireless Micro-segmentationDynamically enforces security policies at the wireless edge to prevent lateral movement of threats.
4. Application-Aware Traffic Control
Malicious activity is often hidden in normal network traffic.
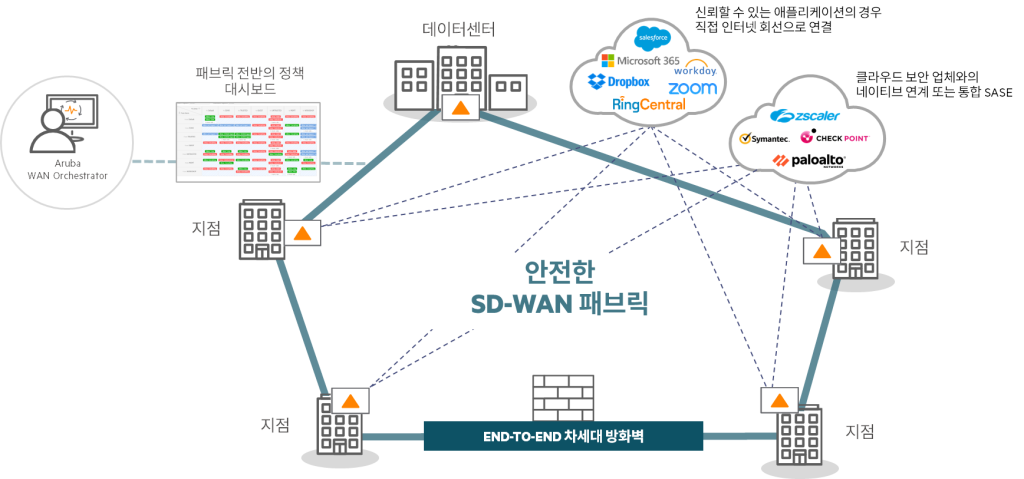
- HPE Aruba Networking EdgeConnect SD-WANDetects and blocks command and control (C2) traffic of ransomware.
- WAN Micro-segmentationPrevents the spread of ransomware across branches, data centers, and cloud environments.
- Encrypted tunnel with zero trust access policyprotects sensitive workloads.
5. ZTNA and Secure Service Edge (SSE)
To prevent overly permissive network access:
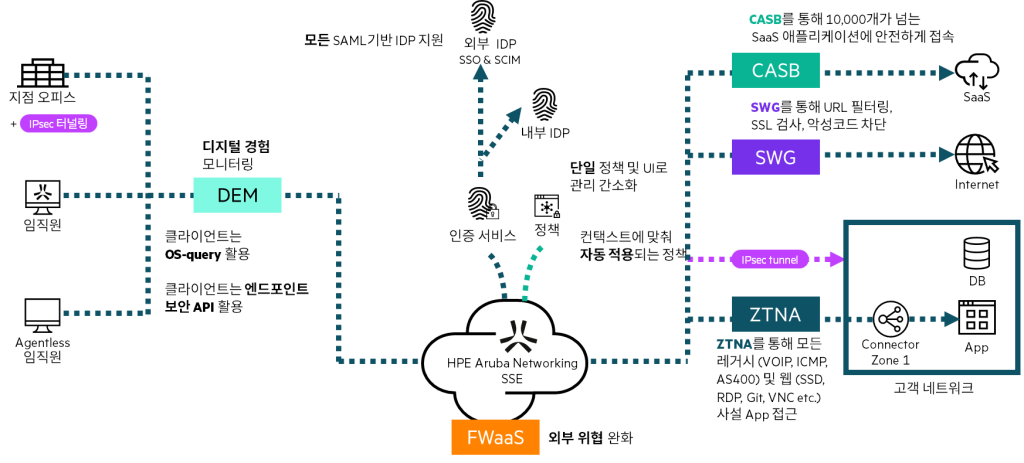
- ZTNAensures that users and devices have access only to the applications they need.
- Secure Web Gateway (SWG)Scans web traffic to detect and block suspicious data transmissions.
- Cloud Access Security Broker (CASB)Monitors and prevents unauthorized firmware updates or malware downloads.
6. AI-based threat detection and response
Automation and AI-powered security reduce threat response times.
- HPE Aruba Networking AI InsightIdentify abnormal network behavior, such as excessive outbound traffic from IoT devices.
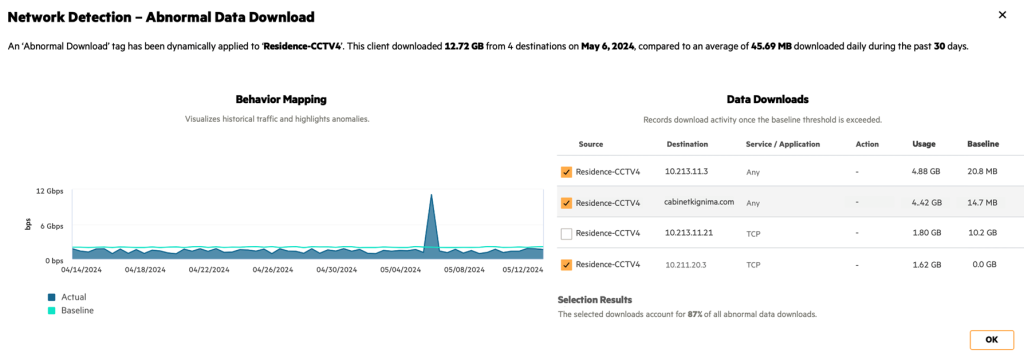
- Network Detection and Response (NDR)Leverages digital twins to visualize potential attack vectors before deployment.
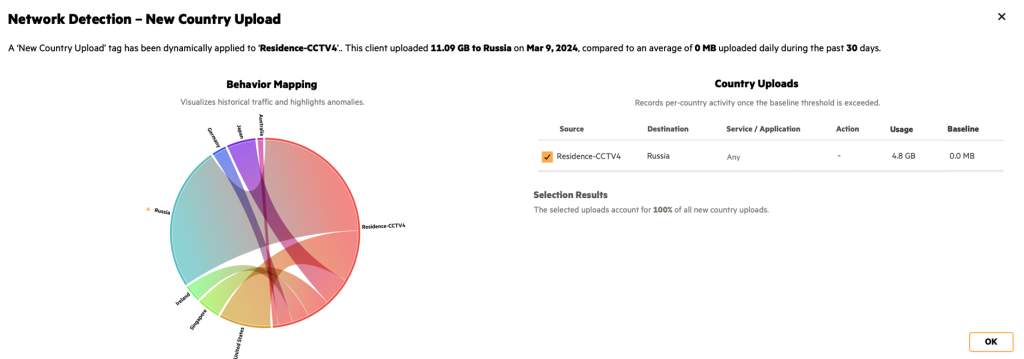
- automated response mechanismsImmediately isolates hacked devices to mitigate damage before the attack spreads.
Step-by-Step Defense Strategy Against Akira Ransomware
HPE Aruba Networking is like Akira A structured defense system to respond to ransomware attacksin the file.
| Attack phase | Zero Trust Solutions |
|---|---|
| hacked webcamIntrusion through | ClearPass NAC blocks untrusted devices Prevent ransomware from entering. |
| Unauthorized network movement | Dynamic Segmentation within the network Prevents lateral movement. |
| Malicious firmware update | SSE CASB blocks unverified downloads Prevent data leaks. |
| Data breach attempt | EdgeConnect SD-WAN/SSE SWG detects and blocks abnormal traffic. Prevent data theft. |
| Preventing the spread of ransomware | HPE Aruba Networking AI isolates infected devices Prevents the attack from spreading. |
conclusion
In today's evolving cyber threat landscape, organizations can no longer rely solely on traditional security models.
HPE Aruba Networking solutions provide businesses with a modern, flexible security approach that reduces risk, promotes compliance, and protects critical digital assets. With AI-powered threat detection, automated response capabilities, and robust network segmentation, HPE Aruba Networking empowers businesses to confidently confront future cybersecurity threats.
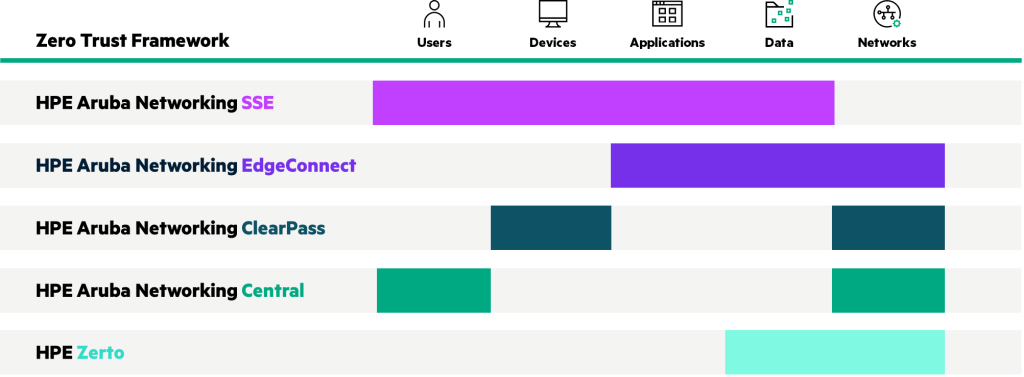
Start today with HPE Aruba Networking solutions The Zero Trust JourneyGet started.
Protect your network, users, and data from advanced threats and secure a secure digital future.


